Information Security Policies and Data Privacy
Since its launch, Licks Attorneys has recognized the importance of a secure operating environment and invested accordingly in information security and safe operating procedures. As the firm has expanded and technology has evolved, we have steadily developed and improved these systems and operating practices.
Licks Attorneys maintains an internal Information Security Systems Policy covering all general security procedures, including specific incident response, business continuity, and disaster recovery plans. This Policy is regularly updated as we continuously monitor and improve both our systems and servers. We will gladly provide a current copy of our Policy for evaluation purposes upon request.
We have also implemented specific internal policies to safeguard the security of our client’s data. This framework is robust but flexible enough to be adapted to your particular requirements with reasonable advance notice.
Our document management system (DMS) iManage, is provided by one of the leading cloud-based document and management services and used by law firms worldwide. The firm’s SaaS (software-as-a-service) solution provides rapid mobility, data security, and digital asset protection for organizations with high data security requirements such as ours.
Additionally, we can provide secure file sharing, storage services, and client portals that guarantee a safe environment for our clients and outside parties who require real-time access to relevant documents located or stored within our servers.
We make document files stored in our document management system, iManageShare, available (usually via *.PDF), employing multi-level file encryption to protect the privacy of content at rest. Data in transit is encrypted to the most stringent industry standards, hosted in Cloud SOC2-certified and ISO 27000 compliant data centers, which enable a high level of security and monitoring. A full audit trail of all actions and comprehensive administrative reporting support and fulfill regulatory and firm governance and audit requirements.
Login at iManageShare is the email address used to receive the message enclosed in the Report. Access requires each user to establish a secure password.
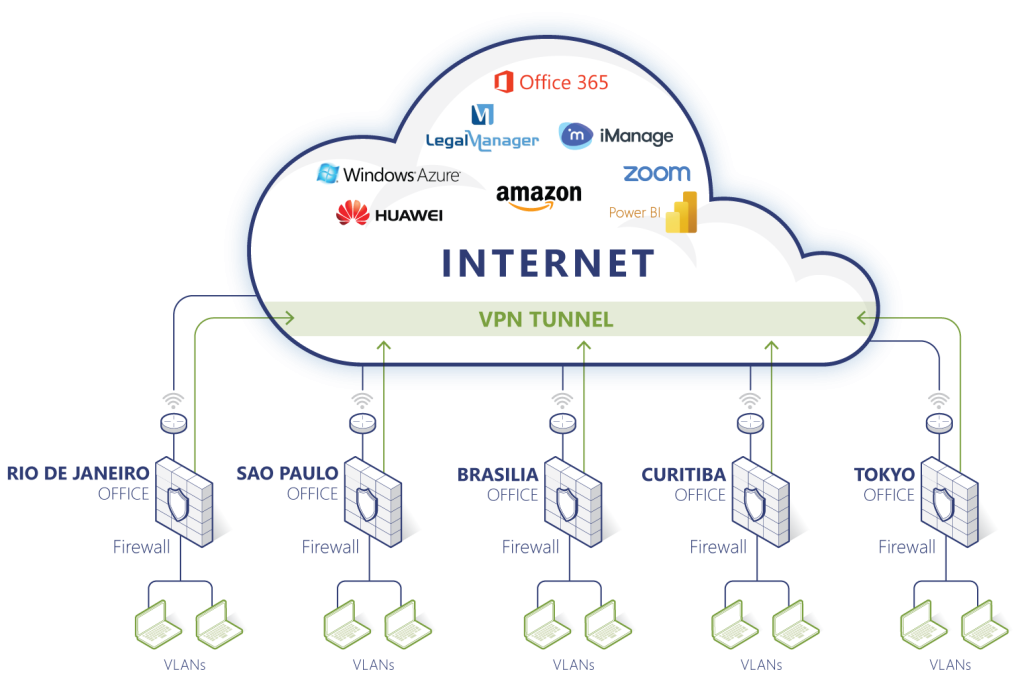
All external connectivity to our servers and files is made through secured VPN systems using cryptography protocols to improve data security. Access to our systems is authenticated by MFA (multiple factor authentication).
We periodically perform penetration and availability tests on our systems, in addition to regular information security training for members and collaborators.
Protecting client information and ensuring the highest standard of service

EXAMPLES OF CURRENT CAPABILITIES AND CERTIFICATIONS IN OUR IT DEPARTMENT

Licks Attorneys operates a state of the art information technology system that guarantees data security and enables us to provide the highest service standards throughout the world. Our entire system, network, and device availability and performance are continuously dashboard-monitored in real-time by our network operations team.
This system is built upon the latest generation hardware, industry-leading service providers, and according to the highest certification standards.
The firm’s web portal servers are deployed through a Content Distribution Network (CDN) hosted by AWS service, which operates at high speed worldwide.
Our hyperconverged servers offer a high level of availability with virtual systems and high-speed infrastructure operating with hardware redundancy and deduplication solution, SSD premium storage arrays with built-in restore backup VM solutions available within 60 seconds.
Our backups systems are made duplicated to a Cloud-based Azure Backup Vault as contingency.
Network security is provided through a Next Generation Firewall.
Our critical system is hosted inside Microsoft’s Azure cloud virtual machines.
The firm’s IP telephone system provides our attorneys with mobility and voicemail messages to their email addresses.
In-office monitoring of our equipment’s electrical sources ensures stability with managed redundancy.
Local network devices by Cisco and Cat6 cabling provide a gigabit-speed intra-office local network.
Internet link redundancy is ensured by various physical means, managed by a SD-WAN automatic balance system.
